Risk management
Message from the Executive Officer
Introducing Enterprise Risk Management to enhance risk response capabilities



Kenichi Morishita
July 2025
Our company faces a variety of new challenges due to rapidly changing international circumstances, economic and social conditions, climate change,and more. To prepare for these challenges, we are promoting the implementation of Enterprise Risk Management (ERM) as a company-wide initiative. Traditionally, we have relied on each business department to act autonomously in this area, but recent environmental changes have led to increasinglybroad and complex risks. ERM will enable us to strengthen our risk response capabilities by centrally identifying risks, and then ensuring our risk responses
are coordinated and mutually complementary across management, corporate departments, and business departments.
Furthermore, we will conduct regular and thorough risk evaluations and assessments to enable rapid response to risks before they manifest, strengthen our information sharing systems, and provide education and training to foster risk awareness among all employees. This will not only increase our ability to predict risks, but also build stakeholder trust and strengthen our foundation for sustainable growth.
We intend to continue developing our ERM on an ongoing basis and strive to bring it to an even more advanced level. I would like to take this opportunity to thank all our stakeholders for their understanding that our risk management system is functioning in a more comprehensive and effective manner, and ask for their continued support.
Approach to risk
In order to appropriately respond to various risks that may arise in achieving our management goals, we will introduce Enterprise Risk Management (ERM) with a preparation period of fiscal 2024 and full-scale implementation from fiscal 2025.
We will define an overall picture of the risks facing our company, visualize the status of risk response, and, through active communication, implement risk management in accordance with the respective roles of business divisions, corporate divisions, and management, leading to the appropriate disclosure of risk-related information.
Governance
Strategy
Enterprise Risk Management (ERM)
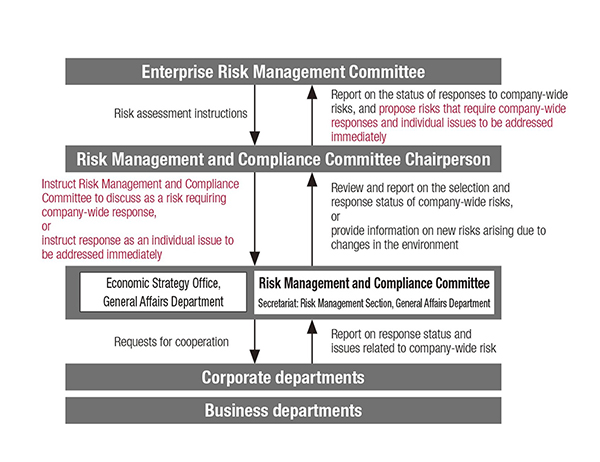
Our comprehensive risk management (ERM) is carried out through appropriate communication between Enterprise Risk Management Committee and Risk Management and Compliance Committee. Based on discussions by management, we categorize risks and issues that require immediate response and company-wide risks that require a company-wide response, and check the status of these responses. In this way, we practice comprehensive risk management that combines responses to risks and issues with company-wide risk management activities.
Risk management
Enterprise Recycling Management (ERM) Activities
ERM activities based on risk issues and activities based on the response status to company-wide risks are both based on one year of risk management activities, and involve a PDCA cycle of identifying risks, assessing them, implementing risk responses, and monitoring and improving the status of risk responses.The Risk Management and Compliance Committee, which is at the center of ERM promotion activities, coordinates the two PDCA cycles and promotes integrated risk management.
●Comprehensive risk management activities


●Comprehensive risk management activity cycle
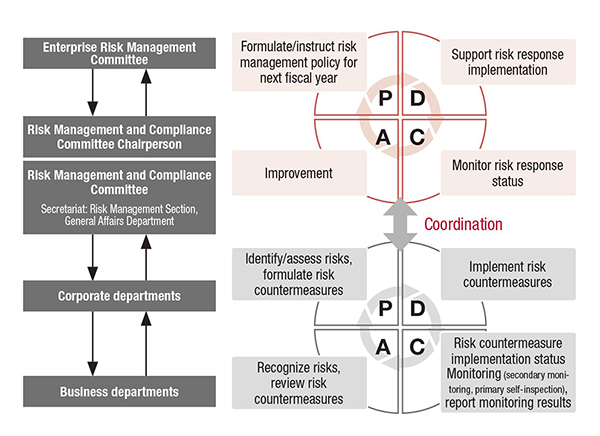


Further strengthening crisis response capabilities
Responding in times of crisis
In our "Crisis Response Regulations" (approved by the president), the Group has established response policies, how to interpret the level of a crisis, communication systems, the establishment of a response headquarters, etc. In the event of a crisis, we will strive to minimize the social impact and damage by taking prompt and appropriate initial measures and responding organizationally with a clear chain of command.
Policy on crisis response (excerpt from Rules on how to deal with a crisis)
(1) Place top priority on safety of all people.
(2) Minimize environmental impact
(3) Sincerely deal with a crisis all the time from the viewpoint of ordinary citizens.
(4) Quickly disclose accurate information.
(5) Retain Company s reliability by carrying out (1) through (4)
●Crisis level
|
|
|
|
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
●Communication system
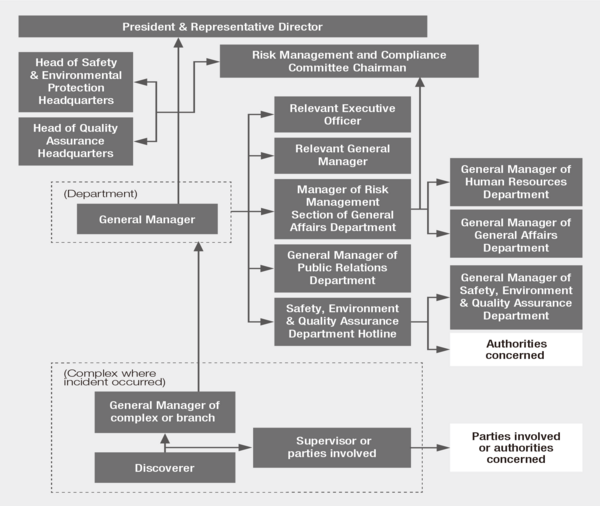
Business Continuity Plan (BCP) initiatives
The Group has formulated BCPs for a Tokyo Metropolitan Earthquake, a Nankai Trough Massive Earthquake, and a new strain of influenza. Comprehensive disaster drills based on each BCP are conducted every year, and cooperation with each base is checked, issues are identified, and the feedback is reflected in revisions to the BCP. At Refineries/Complexes, factories, etc., disaster drills are conducted periodically at all bases based on various crisis response regulations.
In addition, after being designated as a designated public institution by the Cabinet Office in fiscal 2015, we submitted the latest version of our Disaster Prevention Operation Plan in December 2019. As a designated public institution, we are currently proceeding with the emergency vehicle registration of tank trucks in each prefecture.
Implementation of comprehensive disaster prevention training

Comprehensive disaster prevention training (September 2024)
In order to improve the effectiveness of our BCP, we have been conducting comprehensive disaster prevention drills every year since 2007, and the 2024 fiscal year will mark the 18th time the drill has been held.
Based on a scenario that assumes a massive earthquake in the Nankai Trough and a large-scale power outage in the Chubu region, and assuming that the Japan Meteorological Agency issues a "Nankai Trough Earthquake Emergency Information (Massive Earthquake Alert)," we confirmed how to respond to a complex disaster. 193 participants from the head office (Disaster Management Headquarters), related branches, and manufacturing bases participated in the training, including information gathering, transmission, and response planning. In addition, the training was divided into two parts, including a scenario of a delayed earthquake (on the west side) occurring three days after the earthquake, and we confirmed the response status under complex assumptions. At the same time, a company-wide safety confirmation training was also conducted, and approximately 8,500 employees, including those from group companies, promptly reported their safety. We are reflecting the issues and realizations gained from the training in our BCP to improve our crisis response capabilities.
Addressing economic security
Our group keeps a close eye on the trends of international affairs on a daily basis, and in light of their impact, we are making the necessary preparations and taking the necessary measures from the perspective of economic security. As part of this, all relevant departments are formulating response measures for various events and cases that occur overseas, conducting training, and raising awareness among related parties regarding safety, asset protection, and securing information and communications.
Furthermore, in accordance with the Economic Security Promotion Act, as an energy supplier, we investigate and respond to risks within our company and in our supply chain. We also work on daily risk management to ensure the business continuity of our group, with an eye on regulatory and policy trends in the United States and other relevant countries.
Evaluation
Obtained the highest rank in the Development Bank of Japan BCM rating.

Joint fire drill with the Tokyo Fire Department at Tokyo oil terminal (June 2022)
In fiscal 2019, we became the first oil wholesaler to receive the highest rank, Rank A, under the Development Bank of Japan Inc.'s (DBJ) BCM Rating Loan system.
Information management/security management
Basic approach
Under our "Basic Information Security Policy," our group strives to ensure the confidentiality of information assets, the availability and integrity of information systems and networks, and utilize information technology to maintain and improve customer service. Information about customers will be appropriately collected and used in accordance with the Customer Information Management Standards, stored in a safe and up-to-date state, and disposed of appropriately. We also conduct e-learning on information security for all IT system users to ensure thorough information management.
Additionally, in order to reduce the impact of increasingly sophisticated cyber-attacks, we have implemented a system-based multi-layered defense system that prevents unauthorized intrusion and the removal of important information.
Policy
Basic policy on information security
1. The Idemitsu Group will ensure the confidentiality of information assets and the availability and integrity of information systems and networks, and will strive to maintain and improve customer services that utilize information technology.
2. We will take appropriate measures to protect customer information from leakage, falsification, destruction, etc.
3. We will ensure the availability, integrity, and confidentiality of information systems and networks, and strive to avoid causing inconvenience to customers, business partners, and other related parties.
4. We will ensure that our employees, temporary staff, and external contractors are aware of the importance of information security through education and awareness-raising activities, and that they are thoroughly informed about the appropriate use of information and information systems.
5. The Idemitsu Group will endeavor to ensure security by conducting regular audits to check and evaluate compliance with the security policy.
Governance
Information management/security management promotion system
In our group, the management department is in charge of information management for the entire group, in accordance with the "Information Management Guidelines" in the President's Approval Regulations. In the unlikely event that an information leak or other serious security incident occurs, it will be reported to the Risk Management and Compliance Committee, etc., in accordance with the "Regulations for Response in the Event of a Crisis" approved by the president, and the committee will take the lead in taking appropriate action. I'll deal with it. The officer in charge of general affairs serves as the chairperson of the Risk Management and Compliance Committee.
Additionally, with the aim of maintaining and improving the security of control systems, we have established a security council and are promoting security measures across the group in an organized and planned manner based on the "Control System Security Guidelines." At our manufacturing sites, we use the PDCA cycle to make continuous improvements and conduct incident response training every year. We also provide control system e-learning for system users and administrators.
●Information management/security management promotion system
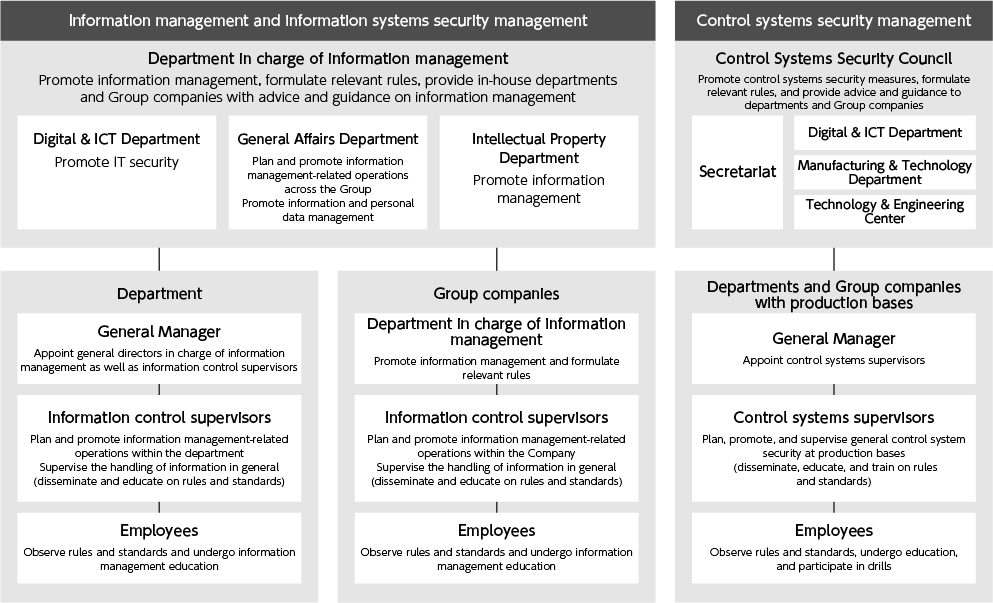


Initiatives
Number of serious information security violations in fiscal 2024: 0
In-house training
Human resource development
ICT including security planning, implementation, and operation * After defining a CDP (career development plan) for human resources, we evaluate the skills and set goals for each individual in the ICT department, and develop human resources in a planned manner.
-
ICT (Information and Communication Technology)
Information Security E-Learning
We conduct information security e-learning (in Japanese, English, and Chinese) every year for all IT system users (employees, temporary workers, outsourced contractors, etc.) to learn about the rules that must be observed. In fiscal 2024, we conducted the training in Korean and Vietnamese in addition to Japanese, English, and Chinese.
Control System E-Learning
Starting in fiscal 2019, we have been conducting e-learning courses on control systems for users and managers of control systems.
|
|
|
|
|
|---|---|---|---|
|
|
Attendance rate: 100% |
Attendance rate: 100% |
Attendance rate: 100% |
|
|
Attendance rate: 100% |
Attendance rate: 100% |
Attendance rate: 100% |
E-learning for web managers
Since fiscal 2019, we have been conducting control system e-learning for users and managers of control systems. In fiscal 2024, we held a training course for those who will take on new roles in charge of web management, with 51 people taking the course.
Security training for digital transformation personnel
Starting in fiscal 2024, we will be promoting the improvement of DX literacy among all employees by offering a basic cybersecurity education program that will enable participants to learn the overview and key points of cybersecurity.
Email training
To raise awareness and reduce the risk of malware infection from targeted email attacks, we conduct targeted email attack drills once a quarter for our company and group companies (including overseas). Additional training is also provided as needed.
Awareness email
We send out a monthly e-mail called the "Cybersecurity Letter" to raise awareness of information security, including the latest information on cyber attacks.
Conducting education and training in preparation for cybersecurity incidents and accidents
In addition to training planned in-house, we also participate every year in the field-wide simultaneous exercises (formerly known as cross-sectoral exercises) hosted by the Cabinet Secretariat's Cybersecurity Center as training to respond to cyber attacks.
Strengthening security measures
Advancement of countermeasures
In order to respond to the increasing risk of cyber attacks, including ransomware attacks, we are promoting system countermeasures such as strengthening user authentication functions and upgrading defense systems, and we are also focusing on developing specialized human resources to prepare for increasingly sophisticated cybercrimes.
Conducting vulnerability assessments
We regularly have third-party security vulnerability assessments conducted at our company. Based on the results of the assessments, we create improvement plans and implement measures in a planned manner.
Privacy protection
Basic approach
Regarding the handling of personal information including specific personal information *1 and anonymously processed information *2 (hereinafter referred to as "personal information, etc."), our group complies with the "Basic Policy on the Protection of Personal Information, etc." (approved by the president) and handles it. We will manage all personal information more safely and appropriately.
-
Individual number and other personal information that includes the individual number
-
Information about an individual obtained by processing personal information so that a specific individual cannot be identified, and the personal information cannot be recovered.
Policy
Basic policy on protection of personal information, etc.
1. Compliance with Laws and Regulations
The Group will comply with the Act on the Protection of Personal Information, the Act on the Use of Numbers to Identify a Specific Individual in Administrative Procedures, other applicable laws, related government and ministry ordinances, guidelines, etc.
2. Matters Concerning Acquisition
The Group will acquire Personal Information, etc. by lawful and fair means. Unless otherwise permitted by applicable laws, the Group will either explicitly explain or announce the purpose of use of Personal Information, etc. to the person in advance, or give notice or announce to the person immediately after acquisition thereof. In addition, the Group will, when acquiring special care-required personal information, obtain the prior consent of the person, unless otherwise permitted by applicable laws.
3. Matters Concerning Use
The Group will use the Personal Information, etc. only within the scope necessary for achieving the purposes of use thereof, unless otherwise permitted by applicable laws.
4. Matters Concerning Provision and Disclosure
Unless otherwise permitted by applicable laws, the Group will not disclose or provide without the consent of the person any Personal Information, etc. to any third party other than outsourcing companies, companies sharing Personal Information, etc., and business successors.
5. Matters Concerning Safety Control Measures
The Group will take the necessary and appropriate safety control measures to prevent unauthorized access to, and loss, destruction, falsification, leakage, etc. of, Personal
Information, etc., and strive to improve personal information protection and management systems on an ongoing basis. The Group will clarify who has the responsibility to protect and manage personal information at each organization and provide the necessary and appropriate education, training and supervision to those employees and outsourcing companies which handle Personal Information, etc.
Furthermore, the Group will keep the Personal Information, etc. accurate and updated. Any Personal Information, etc. with regard to which the purposes of use have been achieved and whose retention period prescribed by applicable laws has expired will immediately be destroyed or eliminated.
In the event of leakage, etc., the Group will immediately take case-by-case correction measures.
6. Matters Concerning Disclosure, etc. of
The Group will respond in accordance with applicable laws to requests for disclosure and correction, etc. (i.e. correction, addition, deletion, suspension of use, elimination, and suspension of provision to a third party), of retained personal data and specific personal information files.
If such data and files are not disclosed or do not exist, the Group will notify the requesting person to that effect.
Governance
Regarding the protection of personal information, the General Affairs Department serves as the secretariat, and information management officers are assigned to each department and group company to promote initiatives. We hold an information management manager meeting every year to provide education within the group.
Initiatives
Number of serious personal information protection violations in fiscal 2024: 0